ModSecurity is an extra layer of defense at your host to protect your websites from malicious code injected into requests. During the Control Web Panel installation, you learned that CWP offers ModSecurity module integration to the webserver.
This article will let you learn more about this security feature. You will get to know what is ModSecurity, how to set it up on the server as well as managing it in CWP and cPanel.

What is ModSecurity?
ModSecurity is an open-source web-based firewall application (WAF) supported by different web servers like Nginx, Apache, IIS. This firewall establishes an external security layer that increases the protection level as well as detects and prevents attacks.
The module also offers HTTP traffic monitoring, logging, and real-time analysis. It encompasses defense from various web-based attacks including code injection and brute force attacks.
ModSecurity supports a flexible rule engine to perform these operations. It comes with a Core Rule Set (CRS) consisting of various rules for:
- Trojans
- SQL injection
- Bad user agents
- Session hijacking
- Cross-website scripting
- A number of other exploits
Request Handling by ModSecurity
https://www.awebsite.com/account.php?username=super'”>DROP%20TABLE%20users–
This is a simple SQL injection attempt to DROP the table users from the database. If you have Mod_security enabled on your server, it will block this script from running.

ModSecurity works in the background. It checks every page request against various rules to filter out those requests which seem malicious. If triggers a 403 Forbidden error if it finds a request malicious.
It simply states that you do not have permission to access / on the server. The path may vary depending on the exact request link. Apart from the 403 Forbidden, the visitor may also receive 404 Not Found or 500 Internal Server Error errors.
Sometimes, due to poor website coding, mod_security may incorrectly determine a legitimate request as malicious. It also causes the visitor to get a 403 error response.
Install ModSecurity in CWP VPS or Server
While installing ModSecurity in CWP VPS is pretty straightforward, this section covers more information than that. First of all, let us see the way to install the module.
Visit the Security → Mod Security menu from the navigation panel in CentOS Web Panel admin. There it will inform that the module isn’t installed.

By default, the module has OWASP old rule engine enabled. But if you have the pro version of CWP then it is best to choose Comodo WAF rules. Finally, click the Install Mod Security Now button. The installation will complete in a bit of time.
Configure Mod Security
There are additional settings on this page to configure the module. The default options are good to let the module work.
The Rules Engine lets you process, not process or process the module in verbose mode. The Audit Log Level describes the level of transactions to log.
Further, you can enable ModSecurity for selected domains only by visiting the Domains tab. There toggle to OFF switch for disabling rules engine for the particular domain.
We had a lot of trouble in managing websites using OWASP old rules because they’re outdated. Even it led us to error 403 (Forbidden) while updating theme/plugin options in WordPress websites. So we had to disable some rules to process legitimate requests.
In contrast, the pro version offers the latest versions of OWASP as well as Comodo WAF with the automatic update feature. These two ModSec Rules fix the problem stated earlier. Hence websites work smoothly.
How to Disable a Rule in CWP ModSec
This is a bit tricky to disable a ModSecurity rule in CWP. First of all, click the Logs tab. In the Find field, type the IP address of the client device which has trouble accessing the domain. Also, select the domain from the dropdown.
Additionally, you can change the number of records by changing the Lines field (20 – 200). Finally, click the search icon. It will list records if there are matching results.
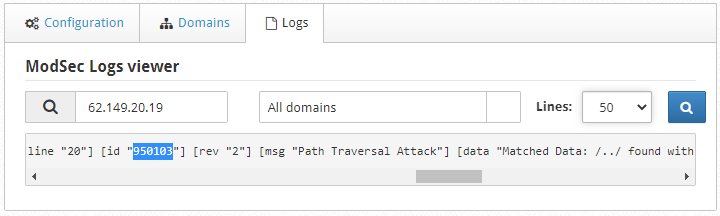
Inspect the line and find the number between double-quotes for the id field as shown in the screenshot above. The number is the rule which requires removal. In the screenshot above, 950103 is the rule id.
Alternatively, if you have SSH access, the following command will quickly find the rule id you need to whitelist
1 | grep 111.222.150.250 /usr/local/apache/domlogs/*error.log|grep ModSecurity |
Just don’t forget to replace 111.222.150.250 with the actual IP address facing the issue.
Disable a Rule Globally
If you want to disable the rule for all domains hosted on the server then add the following line in the global disabled rules file.

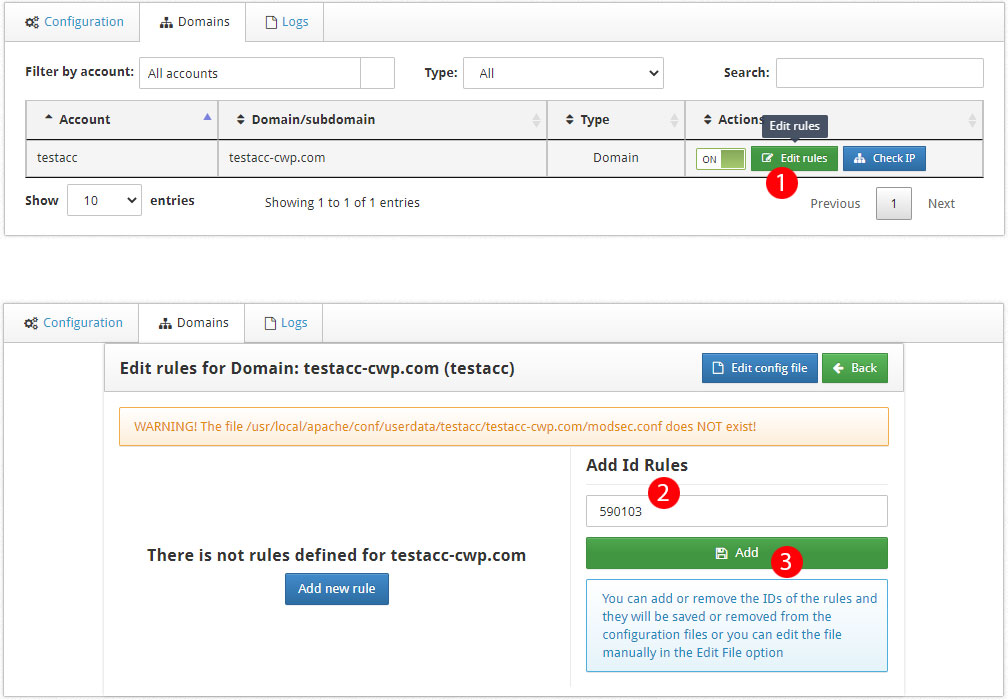
Remove a Rule for a Particular Domain
Or to disable the rule for a specific domain, first click the Edit rule button to open the rule editor. Write the rule id in the Add Id Rules textbox and click the Add button.
Enable (or Disable) ModSecurity in cPanel
Below are simple steps to enable the module in cPanel.

- From the Security section, visit the ModSecurity link.
- Check the status of the module (enabled by default).
- You can completely enable or disable it for your hosting account.
- Or toggle the respective On/Off button to enable/disable the module for a specific domain.

Hope this article helped you understand ModSecurity and installing and managing it in CWP as well as cPanel. Have questions? Ask in the comment form.